The following login authentication methods require that an LDAP object schema be included which supports login. For Unix/Linux and MS/Windows one must include the object classes posixAccount and shadowAccount. (Defined in /etc/openldap/schema/nis.schema)
If using Samba one must also include a schema to support Samba (sambaSamAccount, sambaGroupMapping, sambaUnixIdPool, sambaIdmapEntry, sambaSidEntry, ...) and the appropriate attributes. See schema definition file: /etc/openldap/schema/samba.schema
While LDAP is preferred over NIS (Network Information Services), NIS is supported by legacy Unix systems. For more on NIS authentication and configuration see the YoLinux.com NIS tutorial.
Use command: /usr/bin/authconfig (console) or /usr/bin/system-config-authentication (GUI)
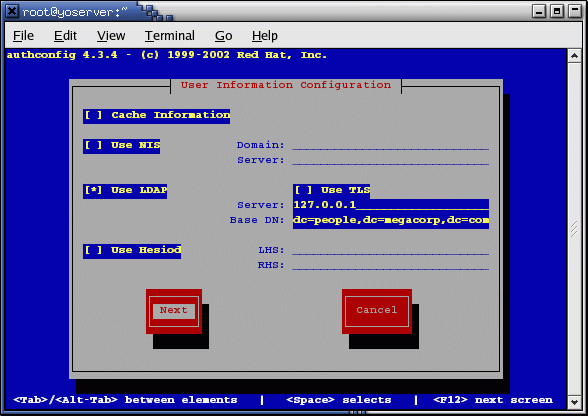
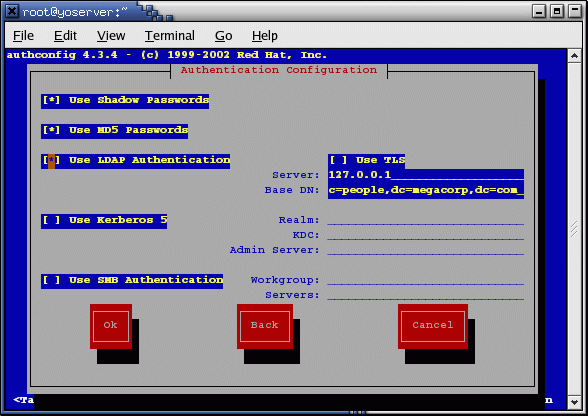
Console screen of /usr/bin/authconfig:
GUI /usr/bin/system-config-authentication:
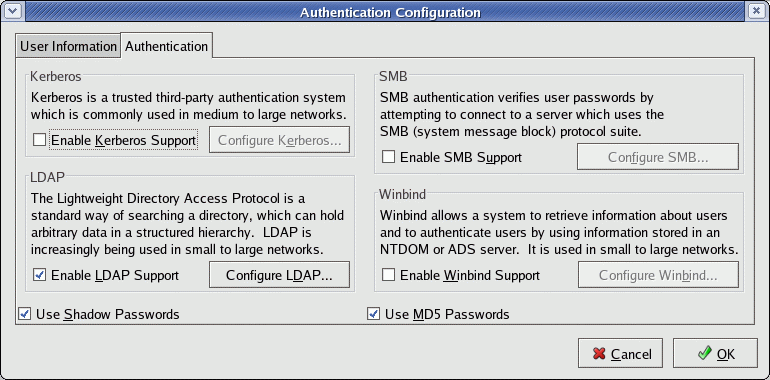
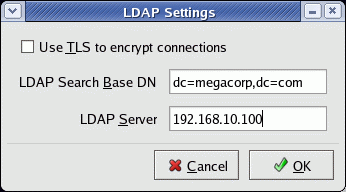
This will create the file: /etc/ldap.conf
host XXX.XXX.XXX.XXX - IP address of LDAP server base dc=domain,dc=org ssl no pam_password md5
If using older SGI MIPS/IRIX systems in the mix you may have to use "clear" instead of "md5".
File: /etc/nsswitch.conf
.. ... passwd files ldap shadow files ldap group files ldap ... ..
[Potential Pitfall]: You may have to reboot in order for LDAP authentication to begin.
[Potential Pitfall]: If using the Sun One LDAP authentication server, note that any entry for the following attributes will result in the requirement that the Linux user change their password each and every time they login. (annoying) Set the following LDAP attributes to blank (not zero):
- shadowmin
- shadowmax
- shadowwarning
[Potential Pitfall]: The user IDs (uid) and group IDs (gid) are cached by the Linux client after authenticating to the LDAP server. If changes are made to the LDAP directory you may have to reboot the client system to pick up the changes. This is also true for NIS authentication.
Note: If using the Linux GUI desktop and mounting Linux home directories to an
NFS server you may have to mount
with the option "nolock". This will be required if the NFS server does
not support rpc.statd or rpc.lockd locking daemons which support
NFS file locking services.
File: /etc/fstab
... nfs-server:/export/home /export/home nfs rw,soft,bg,nolock 0 0 ...
Also be sure to copy essential files and directories from /etc/skel/...which enable desktop use.
Authenticate MS/Windows using PGina: http://www.pgina.org/
Downloads: http://www.pgina.org/?page_id=21
i.e. download pGina: pGina170a.exe
Run pGina170a.exe to install.
Install to C:\pGina and accept defaults.
Download LDAP Auth:
Downloads: LDAP auth plugin
Download instaler i.e.: ldapauth12.exe
Run to install.
Configure pGina: Select: Start + Programs + pGina + Configuration Tool
- Pluggin Path: C:\pGina\plugins\ldapauth\ldapauth_plus.dll
Accept rest of defaults. - Select configure plugin button:
[LDAP configure screenshot]- LDAP Server: IP-address-goes-here
- Port: 389 (default)
- PrePend: uid=
- Append: ou=people,dc=megacorp,dc=com
- Admin User: "cn=AdminManager,dc=megacorp,dc=com"
- Admin password: *******
- Select radio button "Map Mode" then select "OK". (Panel closes)
- Select Save + Exit
(On main config panel)
Uses LDAP "Search mode".
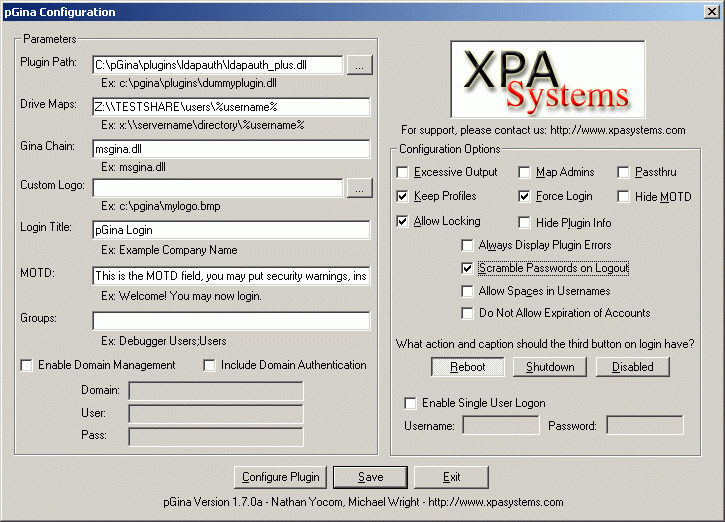
Select option "Scramble Passwords on Logout". This forces LDAP authentication for each login. After an initial login, the login/password become resident locally so that subsequent logins are authenticated locally. This option forces a scramble of the password upon logout forcing Windows/pGina to authenticate with the LDAP server and NOT locally.
Optional test: Download plugin_tester.exe from Pgina LDAP auth
[LDAP authentication test tool screenshot]
- Select: Start + PRograms + pGina + Plugin tester
- Pluggin Path: C:\pGina\plugins\ldapauth\ldapauth_plus.dll
- Use login and passsword to test.
Reconfigure Windows 2000 not to authenticate against PDC:
- Right click on "My Computer" + System Properties
- Select "Network Identification" tab + "Properties" button.
- Select "Workgroup" radio buton and remove workgroup.
- Reboot and you are ready to login with LDAP authentication.
Note:
- Do not use false (which can't be resolved) or a real domain (real or real but fails).
- pGina recognizes local logins if the login id can not be found in the LDAP directory.
- pGina does not support "roaming profile".
To remove pGina: Start + Control Panel + Add/Remove program + select pGina
Links:
Samba and LDAP:
Samba 3.0 can authenticate using LDAP. Download and compile OpenLDAP (even if you are using Sun ONE or some other LDAP server) and the berkley DB source. These libraries will be required when compiling Samba 3.0 for use with LDAP. Compile Samba with the configure option "--with-ldapsam". (./configure --prefix=/opt/samba --with-ldapsam)
We use pGina for login authentication so that all LDAP security rules are followed. (i.e. password length, duration between changes, reuse of passwords, ...) If MS/Windows authenticating with Samba (which in turn is authenticating with LDAP), then many of the LDAP password rules will not be supported. It is for this reason we use pGina. After SAMBA 3.0.7 was available, many of the rules required and supported in pGina are available using SAMBA and the native MS/Windows login. (i.e. Lockout after 5 failed logins) The login/password is held by the MS/windows OS and will be used when accessing Samba shares. Samba will then authenticate the access to the shared drive using LDAP. This replaces the need for a local Samba password database. (created with smbpasswd)
In this configuration we did not use the Samba PDC.
File snippet: smb.conf
... passwd backend = ldapsam: ldap://Ip-address-of-LDAP-server/ ldap admin dn = "cn=sambaadmin, ou=people" ldap suffix = "dc=megacorp,dc=com" ldap user suffix = "ou=people" ...
Note: DNS resolvable names are required for all client and server computers which are part of the Samba domain.
IRIX OS releases and LDAP/PAM:
| IRIX version | PAM comments |
|---|---|
| 6.5.21- | LDAP support No PAM support. |
| 6.5.22 | LDAP support Limited PAM support. Many of the utilities and services were not supported by PAM. |
| 6.5.23+ | LDAP support Full PAM support. |
IRIX 6.5.21 configuration:
Client configuration file: /var/ns/ldap.conf
; SECURITY
security ssl - Options are none or ssl
cipher RSA_RC4_40_MD5
domain - An empty domain identifies the local domain
; LDAP server specifications
server XXX.XXX.XXX.XXX - IP address of LDAP server
version 2 - Open LDAP is considered V2 while Sun One considers themselves to be V3
base "dc=sub-Domain,dc=domain,dc=com"
scope subtree - Options are subtree, onelevel or sbase
password-hash {CRYPT}
binddn "cn=AdminManager,dc=sub-Domain,dc=domain,dc=com"
bindpwd secret-password
Note:
- The "bindpwd" is in clear text and NOT encrypted. When connecting to the server it will use a clear text password. This is required on IRIX 6.5.20.
- {Potential Pitfall]: If no binddn/bindpwd are supplied in this configuration file, then your whole system is opened up for login without authentication. It may look like you logged in with a password but a correct one will not be required. BEWARE!
- See "man ldap.conf" for more information.
LDAP Server: slapd.conf
(Linux: /etc/openldap/slapd.conf)
database ldbm
password-hash {CRYPT}
suffix "dc=sub-Domain,dc=domain,dc=com"
rootdn "cn=AdminManager,"dc=sub-Domain,dc=domain,dc=com"
rootpw {CRYPT}yDtKCHnyyDtKC
Notes:
- Only crypt passwords are allowed in the IRIX implementation. Don't use MD5.
- Note the associations:
Server attribute Client attribute suffix base rootdn binddn rootpw
(crypt)bindpwd
(clear text)
Client nsswitch: /etc/nsswitch.conf
hosts: ldap files nis dns passwd: ldap files(compat) [notfound=return] nis
Note:
- To reactivate new settings:
[root]# nsadmin flush [root]# nsadmin restart
IRIX 6.5.22+ configuration:
Same as above except that the ldap.conf file location is /etc/ldap.conf and the entries "binddn" and "bindpwd" are not required. The entries in /etc/ldap.conf for IRIX 6.5.22+ resemble those for Linux. Bind is done using anonymous bind.
Configure with the Sun SOLARIS admin tool: ldapclient
System Authentication for AIX (and Linux)
It is important to choose the same encryption scheme across platforms. By default Solaris uses CRYPT (DES: Data Encryption Standard) but allows multiple schemes, Redhat and FreeBSD (V4.2+) use MD5 and Suse uses Blowfish.
| Encryption | Hash prefix |
|---|---|
| MD5 | $1$ plus 12 character salt followed by encrypted password. |
| Blowfish (blf) | $2$ or $2a$ plus 16 character salt followed by encrypted password. |
| CRYPT (standard DES) | Two character salt at beginning of hash followed by encrypted password. Does NOT start with "$". (No consistent prefix.) |
| CRYPT (extended DES) | Nine character salt at beginning of hash followed by encrypted password. Does NOT start with "$". (No consistent prefix.) |
Configuration file where encryprion scheme is set:
| OS | Config file |
|---|---|
| RedHat Linux | /etc/libuser.conf /etc/pam.d/system-auth (configured using installation) |
| FreeBSD | /etc/login.conf /etc/auth.conf /etc/master.passwd |
| Solaris | /etc/security/policy.conf See: CRYPT_ALGORITHMS_ALLOW Multiple encryption schemes allowed concurently. |
- Deploying OpenLDAP - Directory Installation and configuration (V1.2 and 2.x)
- Apache and LDAP authentication
- OpenLdap 2.x - SLAPD and LDIF configuration
- OpenLdap 1.2 - SLAPD and LDIF configuration
- LDAP Authentication and user passwords - Adding password protection to LDAP directory.
(Note: This is authentication for the user to access the LDAP database and not using LDAP to authenticate applications) - OpenLdap 1.2 Group security example - SLAPD and LDIF configuration
- Create a new custom object by extending the inetOrgPerson schema
- OpenLDAP 2.x Schema Extension to support MS/Outlook, Netscape 4.5+, PAM,.. (GILSE)
- LDAP admin support scripts and code snippets
- aWebDap - A simple, flexible web front end supporting multiple domains designed for the non-technical user. My favorite, but hey, I wrote it!!
 |
"Understanding And Deploying LDAP Directory Services",
by Timothy A. Howes,Phd, Mark C. Smith and Gordon S. Good, ISBN 0672323168, Addison-Wesley Pub Co Second edition. It is general in nature but complete in that it covers all concepts in depth. It is a good book for those wanting to understand everything about LDAP, schema development and its' capabilities. |

|
 |
"Understanding And Deploying LDAP Directory Services",
by Timothy A. Howes,Phd, Mark C. Smith and Gordon S. Good, ISBN 1-57870-070-1, MacMillan Technical Publishing First edition out of print. (Used only) See second edition above. This is the largest LDAP book I own. It is general in nature but complete in that it covers all concepts in depth. It is NOT a good programmers reference but it is good for those wanting to understand everything about LDAP, schema development and its' capabilities. Netscape centric. |

|
 |
"Programming Directory-Enabled Applications with Lightweight Directory
Access Protocol"
by Timothy A. Howes,Phd and Mark C. Smith ISBN 1-57870-000-0, MacMillan Technical Publishing Excellent programmers reference for those using the LDAP C language API. Also covers search filters and LDAP URL's. The OpenLDAP source code is so poorly commented that I found this book often was the only source for an explanation of what was happening in the code. |

|
 |
"Implementing LDAP",
Mark Wilcok ISBN 1-861002-21-1, WROK Press This book covers all aspects of LDAP from LDIF to the LDAP SDK in C, PERL and JAVA. It has a strong Netscape Directory server bias. |

|
 |
"LDAP System Administration",
Gerald Carter ISBN 1565924916, O'Reilly & Associates This book covers the use of OpenLDAP and the integration of services. |

|
 |
"LDAP Programming, Management and Integration",
Clayton Donley ISBN 1930110405, Manning Publications; 1st edition This book covers LDAP administration as well as introductory information. It covers the directory services markup language (DSML), PERL LDAP module as well as JAVA JNDI. |

|
 |
"Understanding LDAP - Design and Implementation" - IBM-Redbooks
Heinz Johner, Larry Brown, Franz-Stefan Hinner, Wolfgang Reis, Johan Westman IBM Redbook #SG24-4986-00 A reference to ldap, available as PDF as well. This book has a bias towards IBM's E-network LDAP Directory server. Tight, terse, but covers everything. |
|
 |
"LDAP Implementation and Practical Use"
IBM Redbook #SG24-6193-00 |

 Books:
Books: